One of the reasons we launched our Threat Spotlight was to highlight the work of the newest member of our team, Chris Granger, who brings his extensive threat intelligence and hunting experience to Dark Cubed. We’re still a 100% automated threat detection and blocking solution, just like our tagline says, but we’ve reinforced our platform with some human intelligence that enhances our ability to protect our MSP partners’ SMB clients.
What does that actually mean for our customers? Well, here’s the latest example of Chris’ work and its benefit to the Dark Cubed user community.
As a consumer of threat intelligence news, one particular threat caught Chris’ attention over the past few weeks. Namely, an older threat originally discovered in 2014, the Emotet Trojan. The history of this threat and Chris’ detailed analysis can be found below for those interested in diving in headlong, but we’ll try to deliver the Reader’s Digest version for those in our audience for whom time is of the essence.
In a nutshell, Emotet, originally developed as a banking Trojan (malware disguised as a legitimate program) in 2014, has evolved over the years, resurfacing as highly sophisticated phishing malware in early 2021, and remaining active later in 2021 even after some successful law enforcement interdiction efforts.
Why is Emotet of particular concern to Dark Cubed’s MSP partners and their SMB clients?
First, it’s automated and indiscriminate. Emotet is not targeting the large enterprise, mid-enterprise, or small businesses. Its phishing emails are perfectly color-blind; it’s philosophy is “all-of-the-above”, so the SMB community is fair game.
Second, the threat actors deploying Emotet are monetizing their successful network breaches indirectly, selling the access to networks they compromise to (mostly, these days) ransomware operators. (The euphemistic word for this “hacking-as-a-service” cyber crime is “initial access brokering”). As off-the-shelf, user-friendly ransomware software is disturbingly convenient to obtain, there’s no shortage of customers for this potentially highly lucrative access. And, the spectrum of interested cyber-criminal customers extends from those seeking large paydays from deep-pocketed enterprises to those perfectly content with shaking down a small insurance office or accounting firm for ten or twenty thousand dollars. Hence, Dark Cubed’s particular attention to this threat.
So how are we acting on Chris’s Emotet research to protect our MSP partners and their customers? First, we’re identifying if/when Emotet IOCs (indicators of compromise, or IP addresses Emotet perpetrators are operating from) have or are being seen at our customers’ firewalls. Second, we’re developing lists of IOCs that have been affiliated with Emotet operations and assuring they’re appropriately scored and blocked by our platform, so the risk of a successful Emotet attack is minimized for Dark Cubed users.
So, please join me in welcoming Chris to the Dark Cubed team. Even if our clients never meet him, we know they’re going to love him.
Emotet’s Renaissance and Dark Cubed…The Details
Background
Emotet was a banking Trojan when it was first discovered in 2014, but evolved a modular framework and plug-ins to support various objectives like email exfilitration & propagation via spam messages, later via thread hijacking. In 2017 Emotet began evolving again. Seeking to capitalize on the malware’s effective spreading mechanisms and numerous footholds in attractive target networks, Emotet has become a loader used to distribute malware for its operators' clientele.
The Emotet group, now operating as an “Initial Access Broker”, has delivered various Trojans for its partners, such as Qbot, Trickbot and Dridex. Emotet-delivered Trojans have been used to target victim networks with ransomware, such as Ryuk and UmbreCrypt. Beachheads into attractive target networks are also reportedly advertised and sold.
Delivery methods via email have grown increasingly sophisticated, beginning with “pray and spray” spam campaigns, and evolving into automated phishing efforts that leverage victims' mail content, spoofed sender addresses, and target recent correspondents using thread hijacking.
Emotet grew into a prevalent, increasingly dangerous threat, particularly as it showed up more and more as a first stage implant in successful ransomware/data extortion attacks.
In January of 2021, Emotet was disrupted by international law enforcement efforts. After a hiatus, the malware reappeared later in the year, and was reportedly used to install Cobalt Strike Beacon payloads directly.
If this newly observed behavior is an indication of a business model evolving to cater to ransomware actors, Emotet could pose increased risk to a wider range of industry verticals and business sizes.
The Details
DarkCubed has been tracking infrastructure used to distribute malicious email by the Emotet botnet since its resurgence last year. This malspam often originates from servers maintained by Internet hosting companies, which the Emotet group, either by legit purchase or illicit takeover, use to both send out malicious code to victims via email, and control said malicious code, enabling it to download additional malware onto victim machines from these 3rd-party hosted servers.
For example, one of the largest sources of Emotet malspam observed by Dark Cubed in recent months, is a virtual private server (likely compromised) hosted by a Bulgarian cloud hosting provider. This web server reportedly served as a command-and-control server for Emotet, Dridex malware, Bitpaymer ransomware.
Nexuses between the groups associated with the above-mentioned malware have been hypothesized by researchers due to similarities in the loader used by Emotet, Dridex, and BitPaymer.
There may be other links between these groups as well, according to the National CyberSecurity Agency of France (ANSSI):
Evil Corp appears to call on the operators of Emotet (Mummy Spider, Mealybug, TA542) to deliver Dridex as a second payload within the IS that they have already compromised. The operators of TrickBot (Wizard Spider) have the same modus operandi. (THE MALWARE DRIDEX: ORIGINS AND USES)
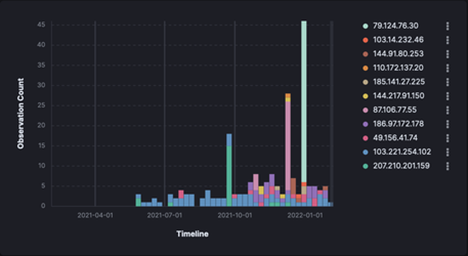
Nevertheless, a connection between cloud hosted infrastructure used to distribute Emotet-dropping maldocs via email, and servers subsequently used to control Emotet once loaded onto victim machines, is clear, particularly when observations of inbound SMTP activity from Emotet command-and-control servers are cross-referenced against public reporting.
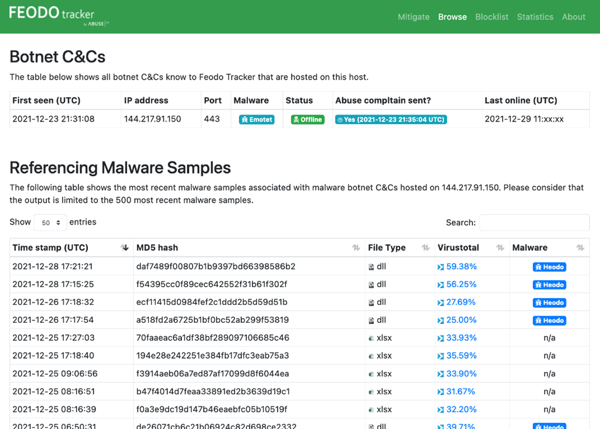
Although the Emotet malware has extensible malware-spamming capabilities, allowing infected devices to propagate the malware via email, compromised or purchased hosted servers, as mentioned above, would be necessary to seed new campaigns.
Once propagated to an initial set of victims, the malspam capabilities of Emotet infections can be leveraged and in cases, may be detected.
Dark Cubed for example, has leveraged behavioral characteristics of the Emotet spambot module to identify infected machines, such as the series of unusual DNS queries issued by the spambot on start-up, as a check for spam filtering.
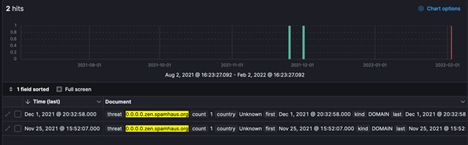
Recently, Dark Cubed has observed Emotet distributing Qbot, Dridex, Trickbot and potentially unidentified malware beaconing to a sinkholed domain.
Using Dark Cubed’s blocklist to prevent inbound SMTP traffic from known Emotet infrastructure may significantly reduce risk from this malware and the menagerie of additional threats it’s used to deliver.

