Gold Cabin, AKA TA551/UNC2420/Shathak, is a theorized Threat Actor responsible for distributing most QBot malware today. Qbot was initially created to steal personal banking information. The backdoor has evolved to become key to an arsenal maintained by those whose business is the illicit side of the cyber arms race. The new purpose of QBot in recent years is to breach as many home and corporate networks as possible, plunder PII and secure “territory” in furtherance of affiliates’ cybercriminal plots, and grow the command-and-control network by which Gold Cabin manages a multimillion dollar, Malware-as-a-Service business empire.
The success and popularity of Gold Cabin as a MaaS provider and the largest distributer of Qbot, is demonstrated not only by our and others’ 12 observations of increases in distribution & infections, but perhaps more worrisomely, in the service’s growing popularity among ransomware groups recently, such as Lockean3, Black Basta, Conti, and others45.
The group appears to be filling a vacuum left by Emotet and has assumed many of TA542’s tactics, such as opportunistically spreading via malspam and using thread-hijacking and automated, context-aware lure creation. However, whereas TA542 used Emotet to break-into networks, Gold Cabin uses two backdoor loaders: IcedID and QBot, in order to gain beachheads into networks, to which additional malware, like Cobalt Strike Beacon, can be deployed. In most ransomware attacks linked to Gold Cabin, however, Qbot has been the more prevalently observed first-stage malware of the two.
Observations: Winter, 2022-23
Celerium has observed Qbot infections using Gold Cabin’s C2 infrastructure in five corporate environments since December of last year. Each QBot implant seems to have been distributed in campaigns that were uniquely distinct vis-à-vis: lure attachment types, exploit vectors, payload delivery methods, evasive techniques, and other characteristics.
VNC Activity
Most recently, Celerium observed a Qbot infection beaconing to Gold Cabin infrastructure and initiating a VNC session with a previously reported Gold Cabin VNC server, earlier this month6. We did not observe activity related to Cobalt Strike Beacon malware in this instance.
VNC server:
78.31.67.7
Victim Becoming a Command-and-Control Server
However, we did observe activity from this infected endpoint that may indicate it was attempted to be converted to a C2 proxy within in the Qbot botnet. As CheckPoint writes7 in their research blog, the process to turn a Qbot-infected host into a C2 proxy server, involves sending crafted UPnP commands to the host’s gateway device to setup port forwarding. The infected host subsequently sends to its C2 server, a list of ports it was able to successfully setup forwarding for. The C2 server responds by attempting to connect via port forwarding, to the victim, using the ports indicated by the victim:
Execute shell commands to allow incoming connections in the host firewall.
Sending crafted UPnP commands to allow port forwarding.
Whenever it creates the opened ports list, the program verifies whether the incoming connection is really allowed by sending the next message to a remote bot and waiting for a connection.
URL – https://<BOT_IP>:<BOT_PORT>/bot_serv
Sample payload:
cmd=1&msg=J3zeJrBLh2sGU4ql0EIr9MncSBCnK&ports=443,995,993,465,
990,22,2222,2078,2083,2087,1194,8443,20,21,53,80,3389,6881,6882,6883,
32100,32101,32102,32103,50000,50001,50002,50003,50010,61200,61201,61202
The remote bot tries to connect using the specified ports to the victim. If the victim receives the data they expected (msg variable), then it’s a sign of a successful incoming connection.
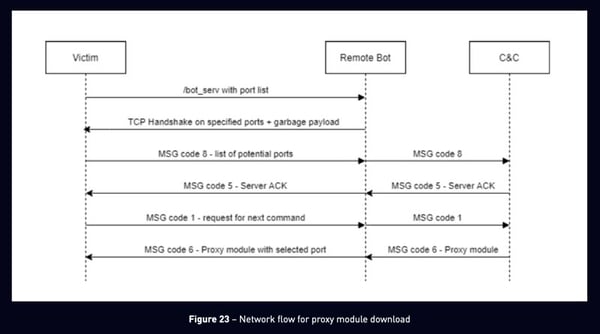
Celerium likely observed step 2 (in the figure above) of this process. Two remote C2 proxy servers ostensibly sent traffic destined to the infected host’s gateway firewall on ports hardcoded to be enumerated by Qbot’s proxy module (443 and 2222/TCP).
Celerium was able to leverage these observations to devise new detection schemes for Qbot proxy module network tests.
Interested in learning more about how Celerium's Cyber Defense Network™ can help protect your organization? Click here.
[1] QBot Malware Infects Over 800 Corporate Users in New, Ongoing Campaign
[2] December 2022’s Most Wanted Malware: Glupteba Entering Top Ten and Qbot in First Place
[3] IDENTIFICATION OF A NEW CYBER CRIMINAL GROUP: LOCKEAN
[4] FBI: ProLock ransomware gains access to victim networks via Qakbot infections
[5] Qbot and Zerologon Lead To Full Domain Compromise
[6] Qakbot infection with Cobalt Strike and VNC activity
[7 ]An Old Bot’s Nasty New Tricks: Exploring QBot’s Latest Attack Methods
